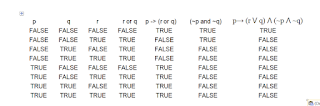
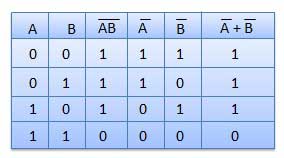
Q.1.
A.1.
Q.2.
A.2.
Introduction
A.3.
Q.4.
A.4.
The e-Business model, like any business model, describes how a company functions; how it provides a product or service, how it generates revenue, and how it will create and adapt to new markets and technologies. It has four traditional components as shown in the figure, The e-Business Model. These are the e-business concept, value proposition, sources of revenue, and the required activities, resources, and capabilities. In a successful business, all of its business model components work together in a cooperative and supportive fashion.
E-Business Concept
The e-business
concept describes the rationale of the business, its goals and
vision, and products or offerings from which it will earn revenue. A successful
concept is based on a market analysis that identifies customers likely to
purchase the product and how much they are willing to pay for it.
Goals And Objectives
The e-Business concept should
be based, in part, on goals such as "become a
major car seller, bank, or other commercial enterprise", and "to
become a competitor to some of the well-known firms in each of these
industries." Objectives are more specific and measurable, such as
"capture 10% of the market", or "have $100 million in revenues
in five years." Whether these goals and objectives are realistic or not,
and whether the company is prepared to achieve these goals is addressed in
the business plan process for startup
firms and in the implementation plan for an
existing firm that is considering a significant change. In looking at the
business model it is sufficient to know what the goals and objectives are, and
whether they are being pursued.
Corporate Strategies
Embedded in the e-Business
concept are strategies that describe how the business concept will be
implemented. These are known as corporate strategies because
they establish how the business is intended to function. These strategies can
be modified to improve the performance of the business. Environmental
strategies, discussed in a following section, describe how the company will
address external environmental factors, over which it has no control.
The E-Business Concept And
Market Research
The selection and refinement of
the business concept should be integrally tied into knowledge of the market it
serves. In performing market research care must be
taken to account for the global reach of the Internet for both customers and
competitors. It is also important to remember that markets shift, and can shift
rapidly under certain conditions. But most important is to truly understand
what the market is, who comprises it, and what do they want.
Figure: The E-Business Concept
A.5.
A.6.
Advantages and disadvantages of knowledge management
Challenges
of knowledge management
A.7.
A.1.
Enterprise
resource planning (ERP) is an enterprise-wide information system
designed to coordinate all the resources, information, and activities needed to
complete business processes such as order fulfillment or billing.
An ERP system supports
most of the business system that maintains in a single database the data needed
for a variety of business functions such as Manufacturing, Supply Chain
Management, Financials, Projects, Human Resources and Customer Relationship Management.
An ERP system is based
on a common database and a modular software design. The common database can
allow every department of a business to store and retrieve information in
real-time. The information should be reliable, accessible, and easily shared.
The modular software design should mean a business can select the modules they
need, mix and match modules from different vendors, and add new modules of
their own to improve business performance.
Ideally, the data for
the various business functions are integrated. In practice the ERP system may
comprise a set of discrete applications, each maintaining a discrete data store
within one physical database.
The term ERP
originally referred to how a large organization planned to use organizational
wide resources. In the past, ERP systems were used in larger more industrial
types of companies. However, the use of ERP has changed and is extremely
comprehensive, today the term can refer to any type of company, no matter what
industry it falls in. In fact, ERP systems are used in almost any type of
organization – large or small.
In order for a
software system to be considered ERP, it must provide an organization with
functionality for two or more systems. While some ERP packages exist that only
cover two functions for an organization (QuickBooks: Payroll & Accounting),
most ERP systems cover several functions.
Today’s ERP systems
can cover a wide range of functions and integrate them into one unified
database. For instance, functions such as Human Resources, Supply Chain
Management, Customer Relations Management, Financials, Manufacturing functions
and Warehouse Management functions were all once stand alone software
applications, usually housed with their own database and network, today, they
can all fit under one umbrella – the ERP system.
ERP –
Implementation is The Challenge
The Ideal ERP System
An ideal ERP system is
when a single database is utilized and contains all data for various software
modules. These software modules can include:
Manufacturing: Some of the functions include;
engineering, capacity, workflow management, quality control, bills of material,
manufacturing process, etc.
Financials: Accounts payable, accounts receivable,
fixed assets, general ledger and cash management, etc.
Human Resources: Benefits, training, payroll, time and
attendance, etc
Supply Chain
Management: Inventory,
supply chain planning, supplier scheduling, claim processing, order entry,
purchasing, etc.
Projects: Costing, billing, activity management,
time and expense, etc.
Q.2.
A.2.
Introduction
When
there are many projects run by an organization, it is vital for the
organization to manage their project portfolio. This helps the organization to
categorize the projects and align the projects with their organizational goals.
Project
Portfolio Management (PPM) is a management process with the help of methods
aimed at helping the organization to acquire information and sort out projects
according to a set of criteria.
Objectives of Project Portfolio Management
Same
as with financial portfolio management, the project portfolio management also
has its own set of objectives. These objectives are designed to bring about
expected results through coherent team players.
When
it comes to the objectives, the following factors need to be outlined.
·
The need to create a descriptive document, which contains vital
information such as name of project, estimated timeframe, cost and business
objectives.
·
The project needs to be evaluated on a regular basis to ensure
that the project is meeting its target and stays in its course.
·
Selection of the team players, who will work towards achieving the
project's objectives.
Benefits of Project Portfolio Management
Project
portfolio management ensures that projects have a set of objectives, which when
followed brings about the expected results. Furthermore, PPM can be used to
bring out changes to the organization which will create a flexible structure
within the organization in terms of project execution. In this manner, the
change will not be a threat for the organization.
The
following benefits can be gained through efficient project portfolio
management:
·
Greater adaptability towards change.
·
Constant review and close monitoring brings about a higher return.
·
Management's perspectives with regards to project portfolio
management is seen as an 'initiative towards higher return'. Therefore, this
will not be considered to be a detrimental factor to work.
·
Identification of dependencies is easier to identify. This will
eliminate some inefficiency from occurring.
·
Advantage over other competitors (competitive advantage).
·
Helps to concentrate on the strategies, which will help to achieve
the targets rather than focusing on the project itself.
·
The responsibilities of IT is focused on part of the business
rather than scattering across several.
·
The mix of both IT and business projects are seen as contributors
to achieving the organizational objectives.
Q.3.A.3.
To facilitate the management decision making at all levels
of company, the MIS must be integrated. MIS units are company wide. MIS is
available for the Top management. Thetop management of company should play an
active role indesigning, modifying and maintenance of the total organization
wide management information system.Information system and Information
technology have become a vital component of any successful business and are
regarded as major functional areas just like any other functional area ofa
business organization like marketing, finance, productionand HR. Thus it is important
to understand the area of information system just like any other functional area
in the business. MIS is important because all
businesses have a needfor information about the tasks which are to be
performed.Information and technology is used as a tool for solvingproblems and
providing opportunities for increasing productivity and quality.Information has
always been important but it has never been so available, so current and so
overwhelming. Efforts have been made for collection and retrieval of information,However,
challenges still remain in the selection analysis and interpretation of the
information that will further improve decision making and productivity.
MIS for a Business Organization :
a. Support the Business Process :
Treats inputs as a request from the customer and outputs as
services tocustomer. Supports current operations and use the system to influence
further way of working.
b. Support Operation of a Business Organization:
MIS supports operations of a business organization by giving
c. To Support Decision Making :
MIS supports the decision making by employee in their daily
operations. MIS also supports managers in decision making to meet the goa lsand
objectives of the organization. Different mathematical models and IT tools are
used for the purpose evolving strategies to meet competitive needs.
d. Strategies for an Organization :
Today each business is running in a competitive
market. MIS supports the organization to evolve appropriate strategies for the
business to assented in a competitive environment.The objective of an MIS
(Management Information System) isto provide information for decision making on
planning,initiating, organizing, and controlling the operations of
the subsystems of the form and to provide a synergetic organization in the
process. Decision Support System: It is sometimes described as the next
evolutionary step after Management Information Systems (MIS) . MIS
support decision making in both structured and unstructured
problem environments.. It supports decision making at all levels of
the organization .IS (Information Systems) are intended to be woven into the fabric of the organizations , not standing
alone.IS support all aspects of the decision making process. MIS are made of
people, computers, procedures, databases,interactive query facilities and so
on. They are intended to be evolutionary/adaptive and easy for people to use.
The human intelligence is closely related with the human experience and decision
making skills which is strongly backed by information's. Now a day's in every
field of human working right information is considered as the most
important resource of good decision making. Every organization runs by the
managers of organization, who are making decisions in every step of
organizational activities. Due to the importance of information in decision
making a separate field has emerged to serve the appropriate information's to
managers for effective and good decision making purpose. Serving the suitable
information use to pass through a process called management information system
as the information is using to make management decisionsQ.4.
A.4.
The e-Business model, like any business model, describes how a company functions; how it provides a product or service, how it generates revenue, and how it will create and adapt to new markets and technologies. It has four traditional components as shown in the figure, The e-Business Model. These are the e-business concept, value proposition, sources of revenue, and the required activities, resources, and capabilities. In a successful business, all of its business model components work together in a cooperative and supportive fashion.
E-Business Concept
The e-business
concept describes the rationale of the business, its goals and
vision, and products or offerings from which it will earn revenue. A successful
concept is based on a market analysis that identifies customers likely to
purchase the product and how much they are willing to pay for it.
Goals And Objectives
The e-Business concept should
be based, in part, on goals such as "become a
major car seller, bank, or other commercial enterprise", and "to
become a competitor to some of the well-known firms in each of these
industries." Objectives are more specific and measurable, such as
"capture 10% of the market", or "have $100 million in revenues
in five years." Whether these goals and objectives are realistic or not,
and whether the company is prepared to achieve these goals is addressed in
the business plan process for startup
firms and in the implementation plan for an
existing firm that is considering a significant change. In looking at the
business model it is sufficient to know what the goals and objectives are, and
whether they are being pursued.
Corporate Strategies
Embedded in the e-Business
concept are strategies that describe how the business concept will be
implemented. These are known as corporate strategies because
they establish how the business is intended to function. These strategies can
be modified to improve the performance of the business. Environmental
strategies, discussed in a following section, describe how the company will
address external environmental factors, over which it has no control.
The E-Business Concept And
Market Research
The selection and refinement of
the business concept should be integrally tied into knowledge of the market it
serves. In performing market research care must be
taken to account for the global reach of the Internet for both customers and
competitors. It is also important to remember that markets shift, and can shift
rapidly under certain conditions. But most important is to truly understand
what the market is, who comprises it, and what do they want.
Figure: The E-Business Concept
A.5.
OLAP The term, of course, stands for ‘On-Line Analytical
Processing’. But that is not only a definition; it’s not even a clear
description of what OLAP means. It certainly gives no indication of why you
would want to use an OLAP tool, or even what an OLAP tool actually does. And it
gives you no help in deciding if a product is an OLAP tool or not.
We hit this problem as soon as we started researching The OLAP Report in late 1994 as we needed to decide which products fell into the category. Deciding what is an OLAP has not got any easier since then, as more and more vendors claim to have ‘OLAP compliant’ products, whatever that may mean (often they don’t even know). It is not possible to rely on the vendors’ own descriptions and membership of the long-defunct OLAP Council was not a reliable indicator of whether or not a company produces OLAP products. For example, several significant OLAP vendors were never members or resigned, and several members were not OLAP vendors. Membership of the instantly moribund replacement Analytical Solutions Forum was even less of a guide, as it was intended to include non-OLAP vendors.
The Codd rules also turned out to be an unsuitable way of detecting ‘OLAP compliance’, so we were forced to create our own definition. It had to be simple, memorable and product-independent, and the resulting definition is the ‘FASMI’ test. The key thing that all OLAP products have in common is multidimensionality, but that is not the only requirement for an OLAP product.
Online Analytical Processing, or OLAP is an approach to quickly provide answers to analytical queries that are multidimensional in nature. OLAP is part of the broader category business intelligence, which also encompasses relational reporting and data mining. The typical applications of OLAP are in business reporting for sales, marketing, management reporting, business process management (BPM), budgeting and forecasting, financial reporting and similar areas. The term OLAP was created as a slight modification of the traditional database term OLTP (Online Transaction Processing).
Databases configured for OLAP employ a multidimensional data model, allowing for complex analytical and ad-hoc queries with a rapid execution time. They borrow aspects of navigational databases and hierarchical databases that are speedier than their relational kin. Drill down in EIS
An Executive Information System (EIS) is a type of management information system intended to facilitate and support the information and decision making needs of senior executives by providing easy access to both internal and external information relevant to meeting the strategic goals of the organization. It is commonly considered as a specialized form of a Decision Support System (DSS).
The emphasis of EIS is on graphical displays and easy-to-use user interfaces. They offer strong reporting and drill-down capabilities. In general, EIS are enterprise-wide DSS that help top-level executives analyze, compare, and highlight trends in important variables so that they can monitor performance and identify opportunities and problems. EIS and data warehousing technologies are converging in the marketplace.
In recent years, the term EIS has lost popularity in favour of Business Intelligence (with the sub areas of reporting, analytics, and digital dashboards).
EIS enables executives to find those data according to user-defined criteria and promote information- based insight and understanding. Unlike a traditional management information system presentation, EIS can distinguish between vital and seldom-used data, and track different key critical activities for executives, both which are helpful in evaluate if the company is meeting its corporate objectives. After realizing its advantages, people have applied EIS in many areas, especially, in manufacturing, marketing,and finance areas.
Basically, manufacturing is the transformation of raw materials into finished goods for sale, or intermediate processes involving the production or finishing of semi-manufactures. It is a large branch of industry and of secondary production. Manufacturing operational control focuses on day-to-day operations, and the central idea of this process is effectiveness and efficiency. To produce meaningful
managerial and operational information for controlling manufacturing operations, the executive has to make changes in the decision processes. EIS provides the evaluation of vendors and buyers, the evaluation of purchased materials and parts, and analysis of critical purchasing areas. Therefore, the executive can oversee and review purchasing operations effectively with EIS. In addition, because production planning and control depends heavily on the plant’s data base and its communications with all manufacturing work centers, EIS also provides an approach to improve production planning and control.
The future of executive info systems will not be bound by mainframe computer systems. This trend allows executives escaping from learning different computer operating systems and substantially decreases the implementation costs for companies. Because utilizing existing software applications lies in this trend, executives will also eliminate the need to learn a new or special language for the EIS package. Future executive information systems will not only provide a system that supports senior executives, but also contain the information needs for middle managers. The future executive information systems will become diverse because of integrating potential new applications and technology into the systems, such as incorporating artificial intelligence (AI) and integrating multimedia characteristics and ISDN technology into an EIS.
In tandem with the growth of the Internet and e-business, the number of digital data sources has increased immensely. These data sources contain important transactional data and are generally interconnected via a network. This has created a pressing need for a suitable executive information system (EIS) that is capable of extracting data from internal and external data sources and providing data analysis on demand for business executives. On-demand data analysis requires an information integration approach that can manage rapid changes in data sources. Existing EISs commonly adopt data warehousing technology to consolidate data from multiple sources in a tailor-made fashion, and support predefined multidimensional data analysis. However, this architecture is neither adaptable to changes in local sources nor flexible enough for ad hoc analyses. This paper develops methods and algorithms for a new EIS architecture that takes advantage of a meta-database to achieve adaptability and flexibility. A PC-based prototype is built to prove the concept.
Q.6.We hit this problem as soon as we started researching The OLAP Report in late 1994 as we needed to decide which products fell into the category. Deciding what is an OLAP has not got any easier since then, as more and more vendors claim to have ‘OLAP compliant’ products, whatever that may mean (often they don’t even know). It is not possible to rely on the vendors’ own descriptions and membership of the long-defunct OLAP Council was not a reliable indicator of whether or not a company produces OLAP products. For example, several significant OLAP vendors were never members or resigned, and several members were not OLAP vendors. Membership of the instantly moribund replacement Analytical Solutions Forum was even less of a guide, as it was intended to include non-OLAP vendors.
The Codd rules also turned out to be an unsuitable way of detecting ‘OLAP compliance’, so we were forced to create our own definition. It had to be simple, memorable and product-independent, and the resulting definition is the ‘FASMI’ test. The key thing that all OLAP products have in common is multidimensionality, but that is not the only requirement for an OLAP product.
Online Analytical Processing, or OLAP is an approach to quickly provide answers to analytical queries that are multidimensional in nature. OLAP is part of the broader category business intelligence, which also encompasses relational reporting and data mining. The typical applications of OLAP are in business reporting for sales, marketing, management reporting, business process management (BPM), budgeting and forecasting, financial reporting and similar areas. The term OLAP was created as a slight modification of the traditional database term OLTP (Online Transaction Processing).
Databases configured for OLAP employ a multidimensional data model, allowing for complex analytical and ad-hoc queries with a rapid execution time. They borrow aspects of navigational databases and hierarchical databases that are speedier than their relational kin. Drill down in EIS
An Executive Information System (EIS) is a type of management information system intended to facilitate and support the information and decision making needs of senior executives by providing easy access to both internal and external information relevant to meeting the strategic goals of the organization. It is commonly considered as a specialized form of a Decision Support System (DSS).
The emphasis of EIS is on graphical displays and easy-to-use user interfaces. They offer strong reporting and drill-down capabilities. In general, EIS are enterprise-wide DSS that help top-level executives analyze, compare, and highlight trends in important variables so that they can monitor performance and identify opportunities and problems. EIS and data warehousing technologies are converging in the marketplace.
In recent years, the term EIS has lost popularity in favour of Business Intelligence (with the sub areas of reporting, analytics, and digital dashboards).
EIS enables executives to find those data according to user-defined criteria and promote information- based insight and understanding. Unlike a traditional management information system presentation, EIS can distinguish between vital and seldom-used data, and track different key critical activities for executives, both which are helpful in evaluate if the company is meeting its corporate objectives. After realizing its advantages, people have applied EIS in many areas, especially, in manufacturing, marketing,and finance areas.
Basically, manufacturing is the transformation of raw materials into finished goods for sale, or intermediate processes involving the production or finishing of semi-manufactures. It is a large branch of industry and of secondary production. Manufacturing operational control focuses on day-to-day operations, and the central idea of this process is effectiveness and efficiency. To produce meaningful
managerial and operational information for controlling manufacturing operations, the executive has to make changes in the decision processes. EIS provides the evaluation of vendors and buyers, the evaluation of purchased materials and parts, and analysis of critical purchasing areas. Therefore, the executive can oversee and review purchasing operations effectively with EIS. In addition, because production planning and control depends heavily on the plant’s data base and its communications with all manufacturing work centers, EIS also provides an approach to improve production planning and control.
The future of executive info systems will not be bound by mainframe computer systems. This trend allows executives escaping from learning different computer operating systems and substantially decreases the implementation costs for companies. Because utilizing existing software applications lies in this trend, executives will also eliminate the need to learn a new or special language for the EIS package. Future executive information systems will not only provide a system that supports senior executives, but also contain the information needs for middle managers. The future executive information systems will become diverse because of integrating potential new applications and technology into the systems, such as incorporating artificial intelligence (AI) and integrating multimedia characteristics and ISDN technology into an EIS.
In tandem with the growth of the Internet and e-business, the number of digital data sources has increased immensely. These data sources contain important transactional data and are generally interconnected via a network. This has created a pressing need for a suitable executive information system (EIS) that is capable of extracting data from internal and external data sources and providing data analysis on demand for business executives. On-demand data analysis requires an information integration approach that can manage rapid changes in data sources. Existing EISs commonly adopt data warehousing technology to consolidate data from multiple sources in a tailor-made fashion, and support predefined multidimensional data analysis. However, this architecture is neither adaptable to changes in local sources nor flexible enough for ad hoc analyses. This paper develops methods and algorithms for a new EIS architecture that takes advantage of a meta-database to achieve adaptability and flexibility. A PC-based prototype is built to prove the concept.
A.6.
Advantages and disadvantages of knowledge management
Consider the measurable benefits of capturing and using
knowledge more effectively in your business. The following are all possible
outcomes:
·
An improvement in the goods or services you offer and the processes that you use to sell
them. For example, identifying market trends before they happen might enable
you to offer products and services to customers before your competitors.
·
Increased customer satisfaction because you have a greater understanding of their
requirements through feedback from customer communications.
·
An increase in the quality of your suppliers, resulting from better awareness of what customers want
and what your staff require.
·
Improved staff productivity, because employees are able to benefit from colleagues'
knowledge and expertise to find out the best way to get things done. They'll
also feel more appreciated in a business where their ideas are listened to.
·
Increased business efficiency, by making better use of in-house expertise.
·
Better recruitment and staffing policies. For instance, if you have increased
knowledge of what your customers are looking for, you're better able to find
the right staff to serve them.
·
The ability to sell or license your knowledge to others. You may be able to use
your knowledge and expertise in an advisory or consultancy capacity. In order
to do so, though, make sure that you protect your intellectual property. See protecting
intellectual property.
Challenges
of knowledge management
In order to maximise the benefit of knowledge management within
your business you may have to overcome the following challenges:
·
Capturing and recording business knowledge - ensure your business has processes in place to
capture and record business knowledge.
·
Sharing information and knowledge – develop a culture within your business for sharing
knowledge between employees.
·
Business strategy and goals –
without clear goals or a business strategy in place for the knowledge gathered
the information will be of no use to your business.
·
Knowledge management systems – these systems can be costly and complex to
understand but when utilised properly can provide huge business benefits. It is
important that staff are fully trained on these systems so that they collect
and record the right data.
Q.7.A.7.
Data
security should be an important area of concern for every small-business owner.
When you consider all the important data you store virtually -- from financial
records, to customers' private information -- it's not hard to see why one
breach could seriously damage your business.
According
to the most recent Verizon Data Breach Investigations Report [PDF], an
estimated "285 million records were compromised in 2008." And 74
percent of those incidents were from outside sources.
We
consulted Roland Cloutier, Chief Security Officer for ADP and a board member
for the National Cyber
Security Alliance, and Matt Watchinski, Senior Director of the
Vulnerability Research Team for cyber security provider Source fire, to find out
the key security measures every small business should be taking.
1. Establish strong passwords
Implementing strong passwords is the easiest thing you can do to strengthen your security.
Cloutier shares his tip for crafting a hard-to-crack password: use a combination of capital and lower-case letters, numbers and symbols and make it 8 to 12 characters long.
According to Microsoft, you should definitely avoid using: any personal data (such as your birthdate), common words spelled backwards and sequences of characters or numbers, or those that are close together on the keyboard.
As for how often you should change your password, Cloutier says that the industry standard is "every 90 days," but don't hesitate to do it more frequently if your data is highly-sensitive.
Another key: make sure every individual has their own username and password for any login system, from desktops to your CMS. "Never just use one shared password," says Cloutier.
And finally, "Never write it down!" he adds.
Implementing strong passwords is the easiest thing you can do to strengthen your security.
Cloutier shares his tip for crafting a hard-to-crack password: use a combination of capital and lower-case letters, numbers and symbols and make it 8 to 12 characters long.
According to Microsoft, you should definitely avoid using: any personal data (such as your birthdate), common words spelled backwards and sequences of characters or numbers, or those that are close together on the keyboard.
As for how often you should change your password, Cloutier says that the industry standard is "every 90 days," but don't hesitate to do it more frequently if your data is highly-sensitive.
Another key: make sure every individual has their own username and password for any login system, from desktops to your CMS. "Never just use one shared password," says Cloutier.
And finally, "Never write it down!" he adds.
2. Put up a strong firewall
In order to have a properly protected network, "firewalls are a must," Cloutier says.
In order to have a properly protected network, "firewalls are a must," Cloutier says.
A
firewall protects your network by controlling internet traffic coming into and
flowing out of your business. They're pretty standard across the board --
Cloutier recommends any of the major brands.
3. Install antivirus protection
Antivirus and anti-malware software are essentials in your arsenal of online security weapons, as well.
Antivirus and anti-malware software are essentials in your arsenal of online security weapons, as well.
"They're
the last line of defense" should an unwanted attack get through to your
network, Cloutier explains.
4. Update your programs regularly
Making sure your computer is "properly patched and updated" is a necessary step towards being fully protected; there's little point in installing all this great software if you're not going to maintain it right.
Making sure your computer is "properly patched and updated" is a necessary step towards being fully protected; there's little point in installing all this great software if you're not going to maintain it right.
"Your
security applications are only as good as their most recent update,"
Watchinski explains. "While applications are not 100 percent fool-proof,
it is important to regularly update these tools to help keep your users
safe."
Frequently
updating your programs keeps you up-to-date on any recent issues or holes that
programmers have fixed.
5. Secure your laptops
Because of their portable nature, laptops are at a higher risk of being lost or stolen than average company desktops. It's important to take some extra steps to make certain your sensitive data is protected.
Because of their portable nature, laptops are at a higher risk of being lost or stolen than average company desktops. It's important to take some extra steps to make certain your sensitive data is protected.
Cloutier
mandates "absolutely: encrypt your laptop. It's the easiest thing to
do."
Encryption
software changes the way information looks on the harddrive so that, without
the correct password, it can't be read.
Cloutier
also stresses the importance of never, ever leaving your laptop in your car,
where it's an easy target for thieves. If you must, lock it in your trunk.
6. Secure your mobile phones
Cloutier points out that smartphones hold so much data these days that you should consider them almost as valuable as company computers -- and they're much more easily lost or stolen. As such, securing them is another must.
Cloutier points out that smartphones hold so much data these days that you should consider them almost as valuable as company computers -- and they're much more easily lost or stolen. As such, securing them is another must.
Q.8.
A.8.
Total cost of ownership (TCO) is an analysis
that places a single value on the complete life cycle of a capital purchase.
This value includes every phase of ownership: acquisition, operation, and the
softer costs of change management that flows down from acquisition such as
documentation and training.
What is included in TCO Analysis?
There are three key components to TCO
calculations:
1.
Acquisition/Physical
Hardware Costs
2.
Operating Costs
3.
Personnel Costs
Let’s look at each of these in turn.
Acquisition Costs
Acquisition/Physical Hardware costs include
the cost of equipment or property before taxes, but after commissions,
discounts, purchasing incentives, and closing costs. Sometimes this will
include one-time peripheral equipment or upgrades necessary to installation or
utilization of the asset.
Operating Costs
Operating costs include subscriptions or
services needed to put the item into business use. This includes utility costs,
direct operator labor, and initial training costs.
Personnel Costs
Personnel overhead may include administrative
staffing, support personnel to the equipment, facility housing the equipment
and operators. This may include ongoing training and troubleshooting labor for
maintenance purposes.
Accounting Contributions
True total cost can include not only costs but
incremental savings or revenue flows created by the capital investment. The
change in cash flows versus the "business as usual" option is what
mitigates total cost of ownership (TCO). Those monies must be valued using Net
Present Value calculations to consider the values over time.
Real total cost of ownership (TCO) analysis is
a critical tool in the decision-making toolbox for any sized business. It
requires both an understanding of the investment considered and the potential
business impact to find the right answer.